November 13, 2025 11:00 am
Register now
Stop fraud before it starts with AI-powered, layered authentication.
interface.ai combines traditional methods (like in- and out-of-wallet questions and OTPs) with cutting-edge tools like secure Device Biometrics and real-time Caller ID Forensics to provide the industry’s most powerful, multi-layered defense.
The AI-powered, risk-based framework dynamically adjusts the level of authentication needed – strengthening protection without adding unnecessary friction for your customers and members.
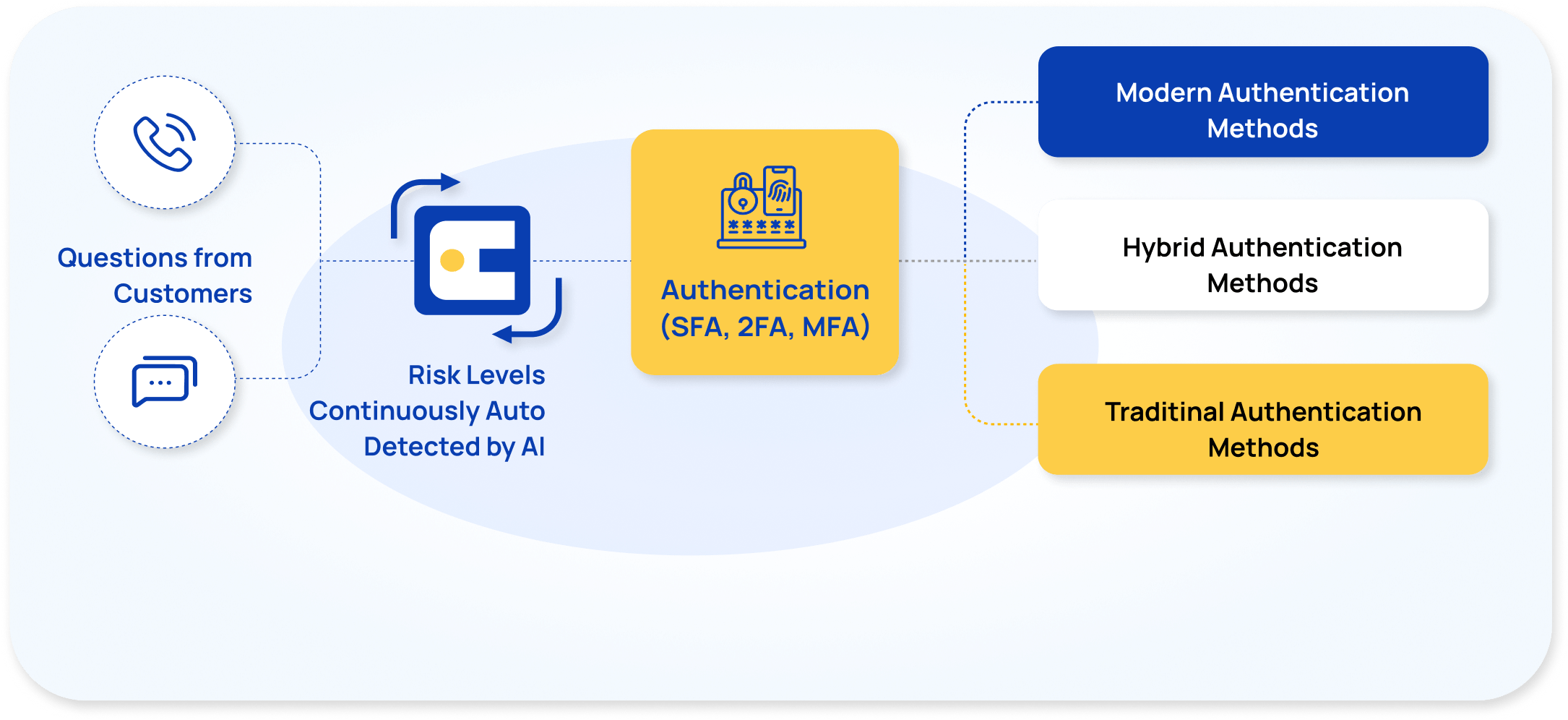
interface.ai Voice AI and Chat AI leverage an adaptive, risk-based authentication framework that intelligently balances user convenience with security. By assessing the context and sensitivity of each interaction, AI Voice and AI Chat apply the appropriate level of authentication—ensuring low-friction access for everyday tasks and stronger protection for high-risk actions.
For informational requests (e.g., branch hours or routing numbers), no authentication is needed, delivering a frictionless, self-service experience
For actions like checking balances or recent transactions, the AI initiates lightweight knowledge-based authentication (e.g., in-wallet or out-of-wallet questions). This is enhanced by passive phone number verification and Caller ID Forensics for calls, providing an added layer of security without disrupting the user.
For high-risk actions like fund transfers or profile updates, the system triggers two-step authentication for maximum security. It uses Caller ID Forensics to detect fraud in real time and Device Biometrics for private, on-device identity verification via Face ID or fingerprint. No biometric data is stored or shared, ensuring full compliance. If biometrics aren’t available, the system seamlessly falls back to an OTP.
Device Biometrics enables secure, low-friction authentication using fingerprint or facial recognition stored on a user’s mobile device. This method ensures high security without requiring users to share or store personal biometric data externally.
When a user calls from a mobile number, the system checks if that number is registered in the core system. Caller ID forensics is performed and shared with agents, but it doesn’t interrupt the flow. If the number is eligible, an authentication link is sent via SMS – users must use the number they called from for security reasons.
To begin the process, the user provides their member or account number and the last four digits of their SSN. Once verified, they receive a link to initiate biometric authentication. After clicking the link, they re-enter their SSN, complete the biometric prompt on their device, and return to the call. From that point forward, the user is registered for device-based biometric authentication.

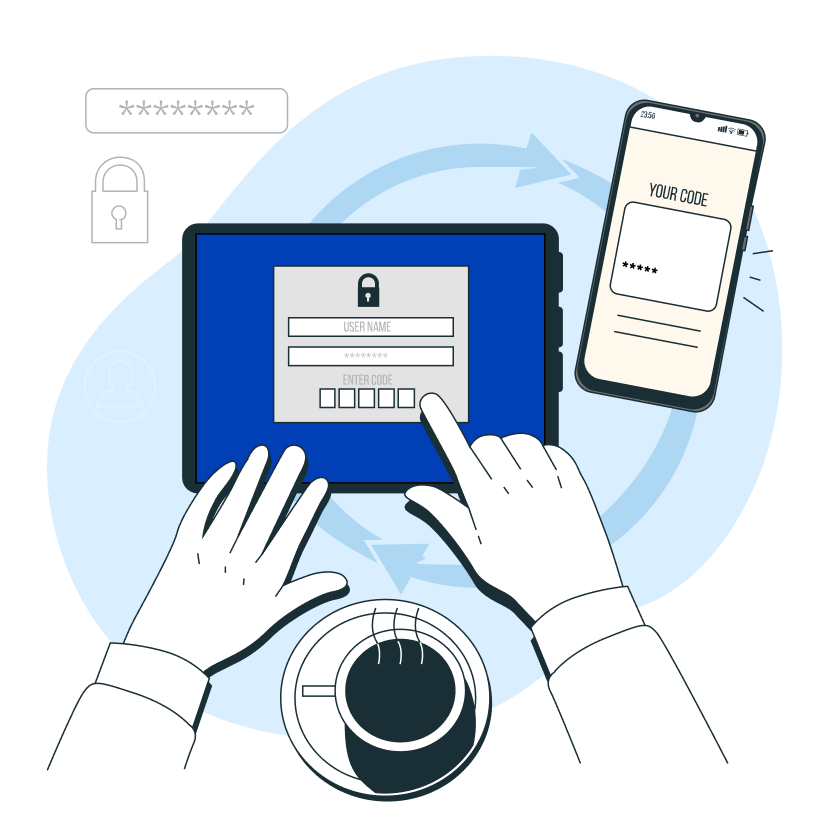
When the user calls from a registered mobile number and if the user is registered for device biometrics, the system sends a biometric authentication link via SMS. The user clicks the link, authenticates using their device’s fingerprint or Face ID, and is prompted to return to the call. Caller ID forensics is again performed and made available to agents during any handoff.
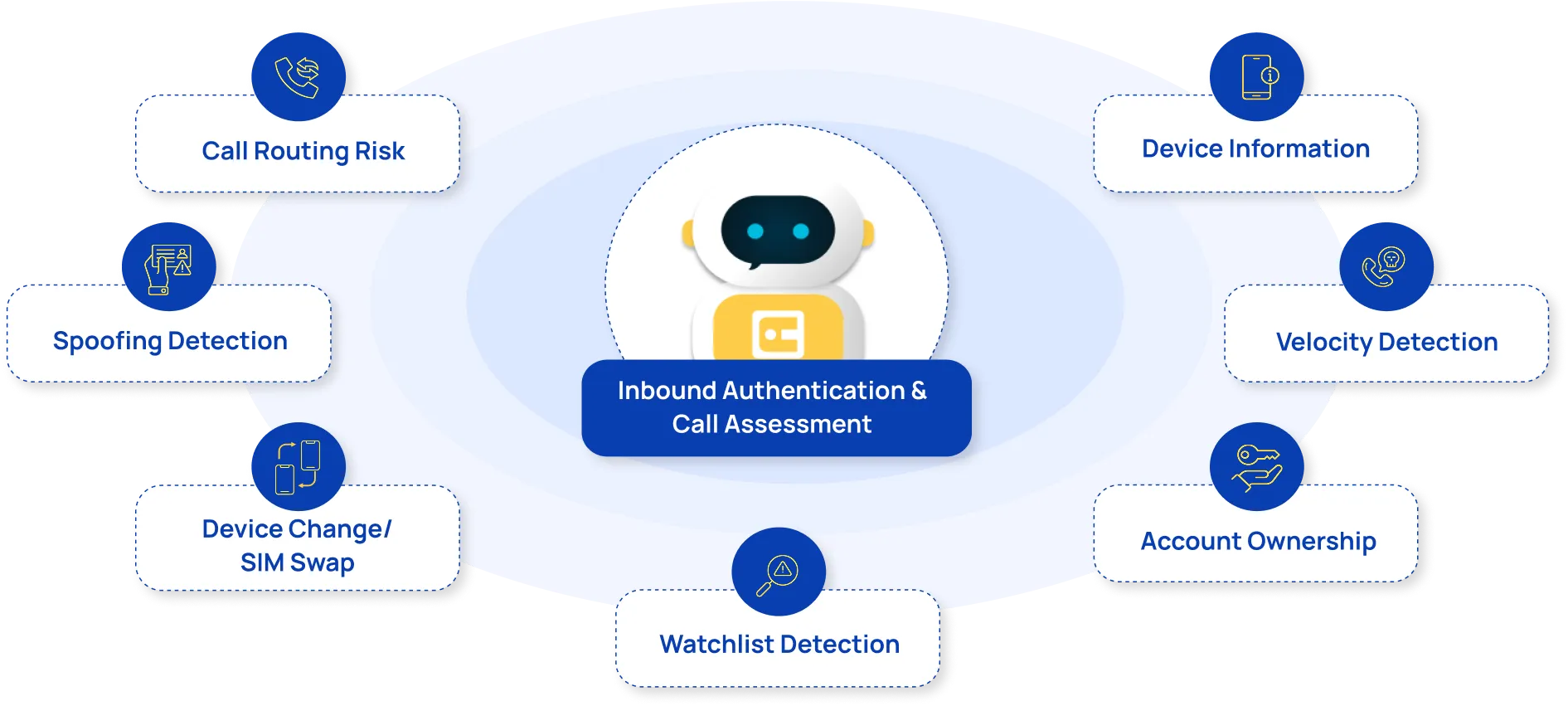
Caller ID Forensics accelerates authentication in the contact center, delivering a seamless, high-confidence identity check that keeps every interaction secure – without slowing members or customers down.
Caller-ID-verified number – The system flags the number as genuine and simply asks the caller for a quick secondary proof (e.g., last four of SSN).
Unverified number – The caller remains unverified and must clear higher-security hurdles such as member ID plus a one-time passcode.
This risk-based flow lets trusted members breeze through with minimal effort while forcing spoofed or suspect calls to scale a much higher wall
Device biometrics offer fast and secure authentication without requiring the customer to share or store any personal biometric data, creating a smooth user experience.
When a handoff is needed, agents receive full context - authentication steps, Caller ID Forensics results, a conversation transcript, and AI-generated resolution suggestions.
Caller ID Forensics automatically scans for 35–40 risk factors to detect spoofed numbers, SIM swaps, or high-risk call origins—flagging threats before they escalate.
Device Biometrics never leave the user’s device. This eliminates the need for storing sensitive data or acquiring consent, significantly reducing compliance and audit overhead.
Authentication adjusts in real-time based on the sensitivity of the customer’s request. Low-risk queries require low authentication, while high-risk actions prompt stronger verification.
The unique combination of real-time Caller ID Forensics with on-device biometrics offers unparalleled fraud prevention—making this solution a clear differentiator in the market.
Utilizes on-device fingerprint or facial recognition for secure, low-friction authentication. No sensitive data is stored or transmitted, ensuring both user privacy and regulatory compliance.

Automatically analyzes 35–40 caller attributes (e.g., burner phones, SIM swaps, spoofed numbers, location mismatches) to identify potential fraud. High-risk calls are flagged for immediate attention.
Continuously evaluates the risk of each customer interaction and applies the appropriate level of authentication—from no-auth for basic FAQs to multi-step verification for sensitive transactions.

Supports in-wallet and out-of-wallet questions, OTPs, and magic links – layered dynamically based on risk level to ensure the right balance of security and member convenience.
Provides agents with a full transcript, authentication summary, Caller ID Forensics results, and an AI-suggested resolution during handoff for faster resolution.

Instantly feeds authentication results and risk scores into the AI agents to power secure, personalized interactions without extra development.
